Signing on Tezos with Android Biometrics | Part 1
Benjamin Fuentes of adoption team Marigold explains how to sign onto Tezos using biometrics.
1,150 words, 6 minute read

Classic signing with a wallet #
As a quick remember, here is the common flow:
The user sends a request to his wallet to sign a payload
The wallet signs the payload with the private key and returns the signature
The user forwards the signed message to a Tezos node
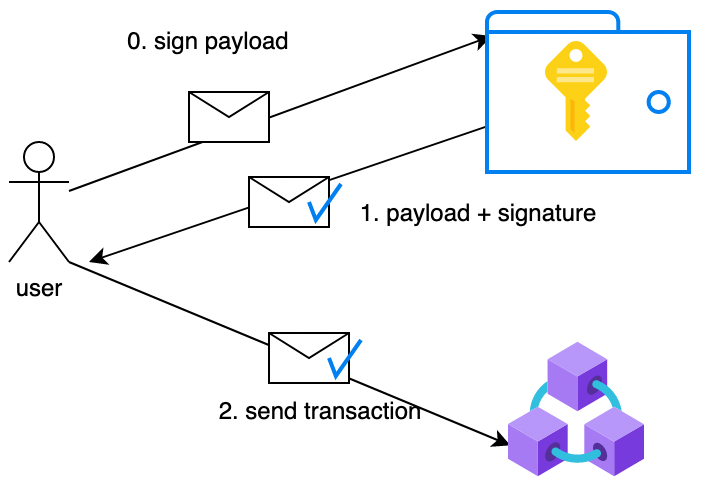
- The wallet can be local or distant.
- If remote, there is a risk over the communication channel and third parties
- Each wallet will use its own mechanism to protect the private key: e.g. password
Biometrics signing #

Biometrics on Android provides a convenient method for authorizing access to private content within your app. Instead of having to remember an account username and password every time they open your app, users can use their biometric credentials to confirm their presence and authorize access to the private content
Your phone, depending on the security level of the chip, becomes your HSM (Hardware Secure Module) replacing external devices like a Ledger or a Yubikey.
There are two approaches on Tezos to use Biometrics:
Solution 1: Use your phone Biometrics to protect the private key #
This solution is similar to the signing with a wallet solution
Details :
- The wallet is the secure chip of the phone, it is a local communication
- The private key is protected by the phone Biometrics
Initialization #

Biometrics just controls the access to the keypair. The keys are generated from a native Android algorithm, a crypto library as spongycastle or just an encrypted private key as string. Once the user has authenticated with Biometrics, he has access to the protected object on the Keystore.
Signing operation #
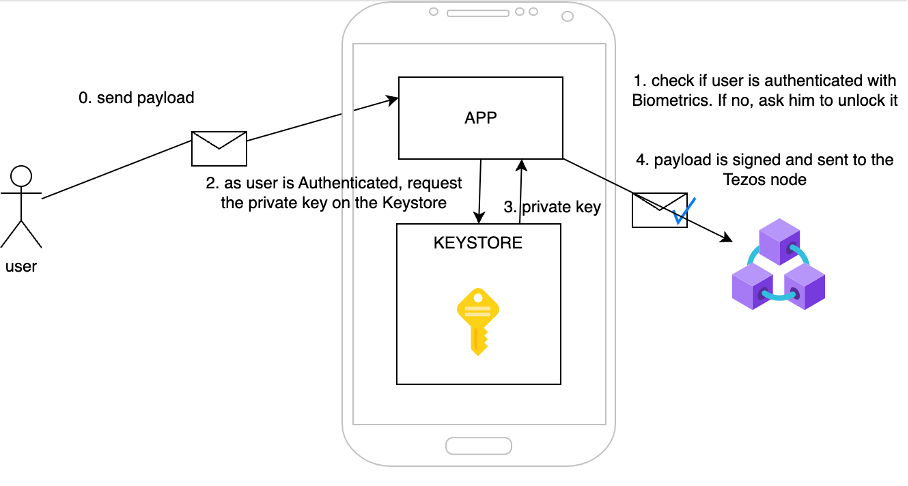
The signing process is possible only if the user is authenticated with Biometrics, otherwise he does not have access to the private key. Signing a payload can be done either using native Crypto libraries or with third-party crypto libs as a lot of Blockchain signing are not compatible with common OS standards.
Example #
Airgap Vault + Airgap Wallet. The solution proposed by Airgap is to split between a Vault app that manages all the keys on the device Keystore protected by Biometrics access and another Wallet app that does the signing part. The solution is multichain and so, can use different signing algorithms.
Demo #
In this video, I am showcasing the below scenario with Android Biometrics with fingerprint access
#
- Open the app
- Generate random Tezos Credentials
- Ask to unlock Biometrics to access the app. Encrypt the Credentials and save it on the Android Shared Preferences (used as a database)
- Alice sends some Tez to our account to have enough cash for us to pay the fees
- Refresh the balance of our account
- Send 1 mutez to Alice. As we have Biometrics unlocked, we could simply fetch the encrypted keypair T on cache, ask the protected keypair N to decrypt the keypair T and then sign the transaction with Taquito
- Verify that Alice received the money
Better alternative: Prevent the private key access itself by Biometrics and use Blockchain crypto algo #
The difference with the previous flow is :
- The Keystore will not send back the private key to the application, instead, it holds and signs directly the payload.
- We do not require another key for encrypting our Tezos key.
- It is impossible to access the private key, only the Cipher object provides the crypto functions and there is no export/import. It requires setting the KeyGenerator this option setUserAuthenticationRequired(true) and pushing the cipher on the Prompt biometricPrompt.authenticate (biometricPromptInfo, BiometricPrompt.CryptoObject(cipher))
- As of today, the native Android crypto lib does not support Tezos signature secp256r1+Blake2B or others. It would require injecting spongycastle crypto lib inside the list of Android-supported algorithms.
It is an extreme case but some applications like Frida can bypass your Biometrics Prompt and look at each object stored on an unprotected KeyStore.
Solution 2: Use WebAuthn Biometrics and a Gas station #
In this solution, you need a relay to sign the final transaction for you. The reason is that your mobile does not have by default the right crypto libraries to do so, but the relayer does. Most phone Biometrics can produce a secp256r1 signature that is the base of the WebAuthn standard, part of the FIDO2 project. It is mostly used today in the industry.
Initialization #
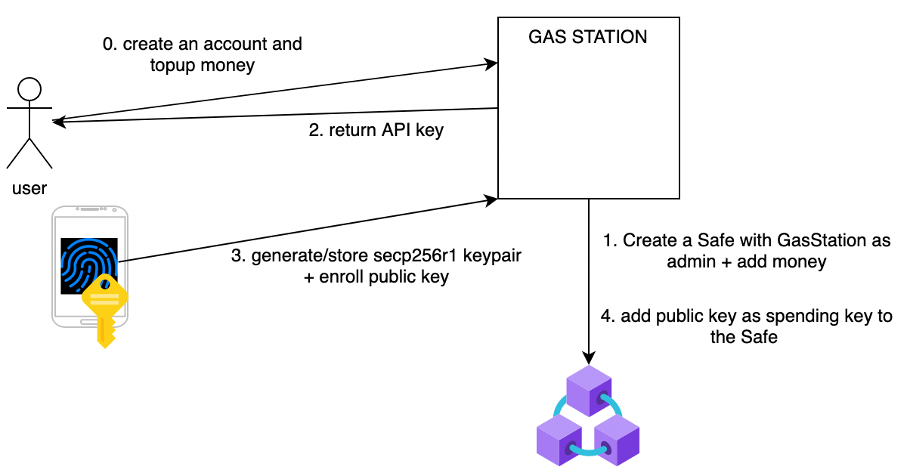
A relayer is required for forwarding to signed payload to the Safe contract. It can also pay the fees, add recovery mechanisms and bring a web2 experience. The private key never leaves the device or is accessible. First, an account has to be created on the service provider and some money has to be sent to configure the Safe smart contract. After enrolling the phone to the platform, authorized devices will be able to interact with the Safe smart contract.
Signing operation #
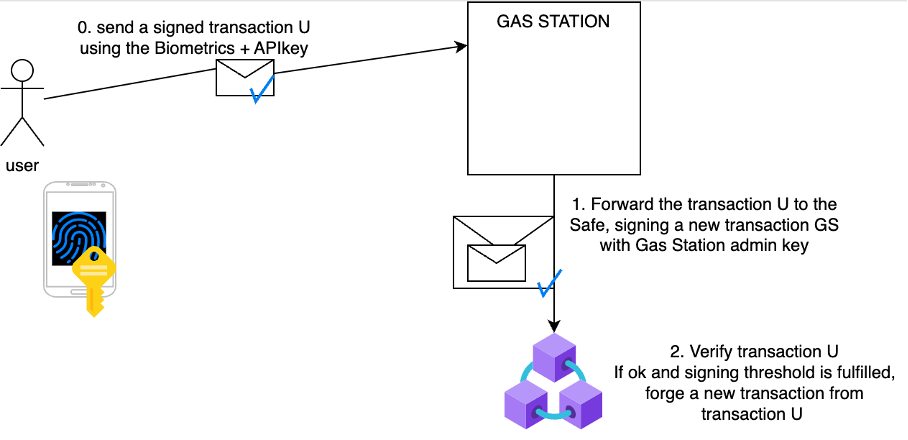
The Gas station API sends the signed payload to a Safe contract for verification via a classic on-chain transaction (There is also an alternative using the Gas Station as a remote signer but in the end, it is the same). The target contract of the transaction has to be compatible with ERC-1271 Standard (transaction signed by smart contracts like a Safe). The fees, and eventually the money transferred, are paid by the Safe and deducted from the user account.
Example #
The Cometh product is implementing this solution on EVM using gnosis Safe and providing gasless feature & recovery (https://www.cometh.io)
On Tezos there is a gasless solution named Gas Station on the Ghostnet network but not based on Biometrics yet. You need to sign Tezos transaction and not transaction using your device’s native crypto algorithms. To implement a similar solution it would be necessary to implement a Ligo version of a p265 Signer and verification for R1 signatures.
Conclusion #
Using your phone Biometrics is the future of web2 and web3 Identity to improve user experience. Until now, the first initiative on wallets came from the web3 using their preferred algorithms led by Blockchain performance constraints. Then the big web2 actors like Google, Apple and Microsoft understood the potential of going password-less (FIDO2, PassKeys and WebAuthN) and pushed it on mobile devices via Secure Enclaves. Today there are still some gaps in web3 wallets not leveraging yet all the potential of Biometrics. On the other side, it is impossible to import/export private keys from the mobile device and this causes a lot of issues for the end user on web2 and web3 for recovery purposes. Still, web3 suffers from a lack of customer knowledge in managing fees and crypto-currencies on a wallet to pay transactions. Maybe the solution is to mix these components:
- Better Biometric support for signing native web3 transactions
- Better gasless and recovery management using Safe smart contracts
This article was originally published as a blog on the [Marigold website](https://www.marigold.dev/post/signing-on-tezos-with-android-biometrics)
 ]
]